Passkeys are right here to switch passwords. When they work, it’s a seamless eyesight of the future. But don’t ditch your outdated logins just nonetheless.
Lock your SIM card. Just as you'll be able to lock your phone, you can also lock the SIM card that is used to discover you, the owner, and to attach you to definitely your cellular network.
You find Peculiar photos and videos in your gallery. If hackers hack your phone, they may possibly utilize it to spy on you or choose photos and videos without your knowledge.
Sideloading, wherein you install apps without an app keep, is additionally a process to manage carefully as a consequence of a lack of foundational safety measures.
“Manufactures have commenced supplying visual clues to buyers, which make it harder for apps to observe you without your knowledge,” Jackson states. “Now, if an attacker is trying to trick you, you’ll no less than know that your camera is on.”
Over the years, Brendan has created about an array of subjects. Be it masking game previews at GamesCom in Germany, listing the best Amazon Key Working day deals, reviewing gaming controllers, Kindles, and folding smartphones, or even Intercontinental guides on buying a mattress - he is nevertheless really aggravated that the UK and US have distinctive measurements and names for them. Much more recently, he is been covering Intercontinental How to observe guides on different sporting gatherings like Formulation 1, tennis, Champions League, cricket, or the most well liked new motion pictures and TV displays. Beyond operate, you will find Brendan attempting to make a dent in numerous watchlists across streaming apps or actively playing games on his Collection X or PS5, typically downloading (hoarding) however far more Game Go games or grumbling about how open up-environment games should be scrapped for just a reliable 10-hour encounter like the Uncharted collection. Read extra
Trojans: Trojans are sorts of malware that can be disguised in your phone to extract critical data, including credit card account aspects or individual data.
These vulnerabilities in smartphone PIN entry raise significant concerns about the security of this authentication process.
Empower biometric safety (like fingerprint ID). If someone steals your phone, it will be Considerably harder to break into it in case you have fingerprint or facial recognition ID enabled.
You’re viewing new apps on your phone. Be Particularly aware of unrecognized or suspicious apps on your property screen. Some destructive apps will put in new apps, with the hacker hoping that you don’t care or notice.
Note: The use of VPNs is unlawful in particular countries, and using VPNs to access region-locked streaming information may possibly represent a breach with the phrases of use for certain services. Organization Insider does not endorse or condone the illegal use of VPNs.
Owing to updates how to remotely hack someones iphone on computers and cell phones, there are easy indicators that let you know when an application has access to the cameras and microphones on your device. Comprehending these signals and maintaining an eye fixed out for them can be an easy way to safeguard yourself.
Want a very good VPN? Take advantage of this are not able to-miss offer you to the best VPN we've examined and used For a long time for Intercontinental streaming and guarding our online privacy.
Automated tests is crucial. But some issues can only be recognized by gurus, and manual penetration screening is really a significant piece of a DevSecOps program.
 Anna Chlumsky Then & Now!
Anna Chlumsky Then & Now! Anthony Michael Hall Then & Now!
Anthony Michael Hall Then & Now! Mackenzie Rosman Then & Now!
Mackenzie Rosman Then & Now!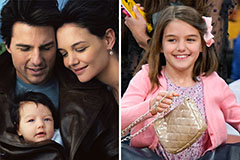 Suri Cruise Then & Now!
Suri Cruise Then & Now! Daryl Hannah Then & Now!
Daryl Hannah Then & Now!